GitLab Integration
This guide explains how to integration the Cremit service with GitLab
Issuing a GitLab Group Access Token
-
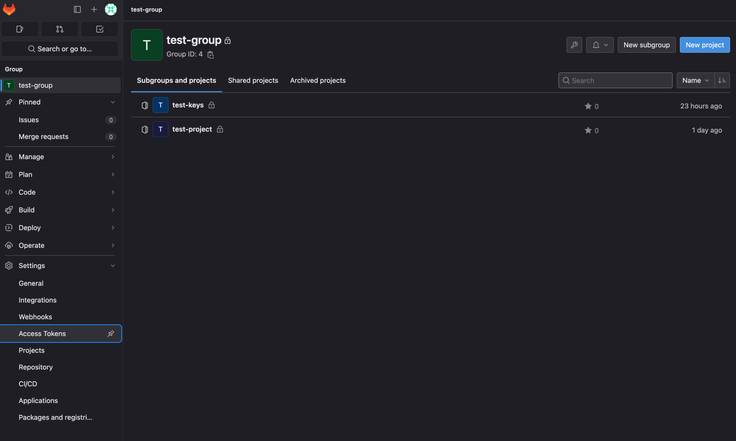
Navigate to the Access Tokens page On the left menu of the group page, go to Settings → Access Tokens.
-
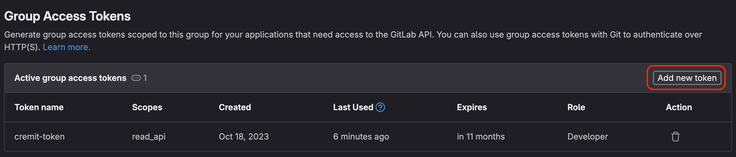
Create a new token Click the Add new token button in the top right corner of the Group Access Tokens page.
-
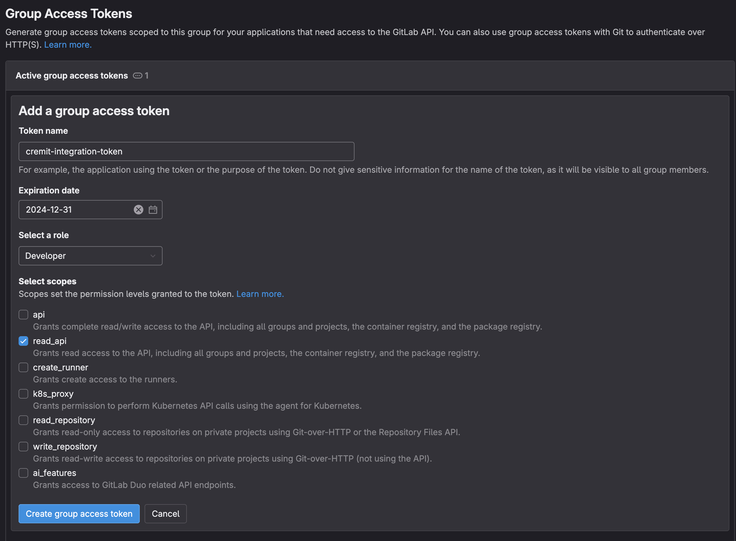
Fill out the form Role: Select a role with at least Developer permissions (required to read repository contents). Scopes: Make sure the read_api scope is enabled (required to list accessible projects). Name: Enter a descriptive name for the token. Expires at: Choose an expiration date for the token (optional).
-
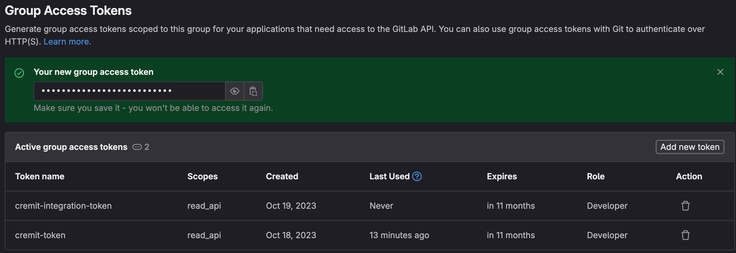
Generate the token Click Create group access token to generate the token.
-
Copy the token The generated token will be displayed on the screen. Copy the token for use in integration settings.
Configuring Integration in Cremit
-
Go to the Integration page On the left menu of Cremit, go to Integration.
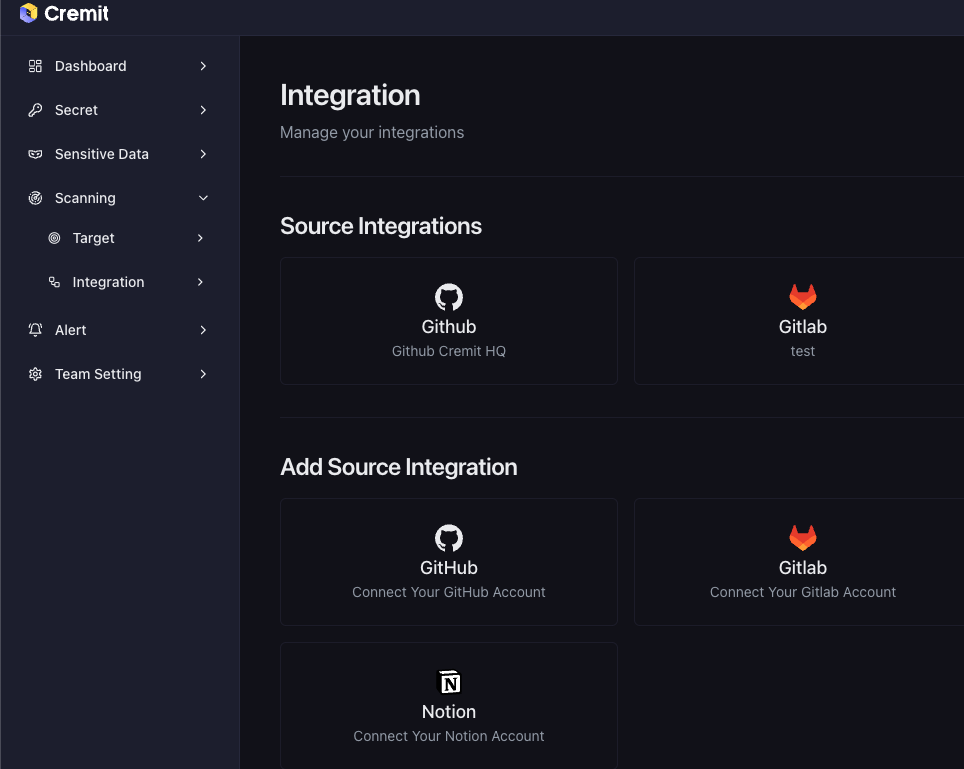
-
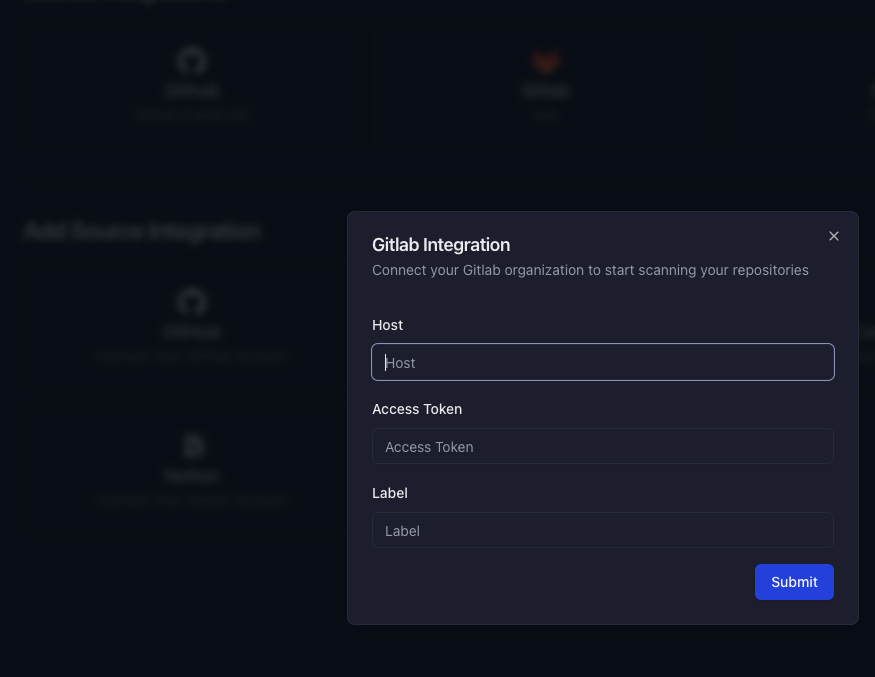
Enter the required information Host: Enter the hostname of your GitLab instance. Group Access Token: Paste the group access token you generated earlier. Label: Enter a label to identify the integration.
-
Complete the integration Click Submit to add the source integration.
Granting multiple project access to a group (Optional)
If you need to grant access to multiple projects to a specific group at once, follow these steps:
3.1 Generating a user access token
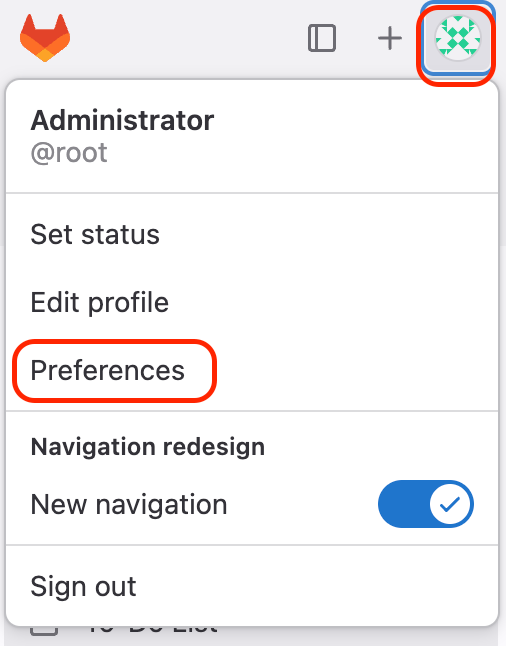
- Log in to GitLab, go to user menu → 'Preferences' → 'Access Tokens'.
- Click 'Add new token', enter a token name, select the 'api' scope, and create the token.
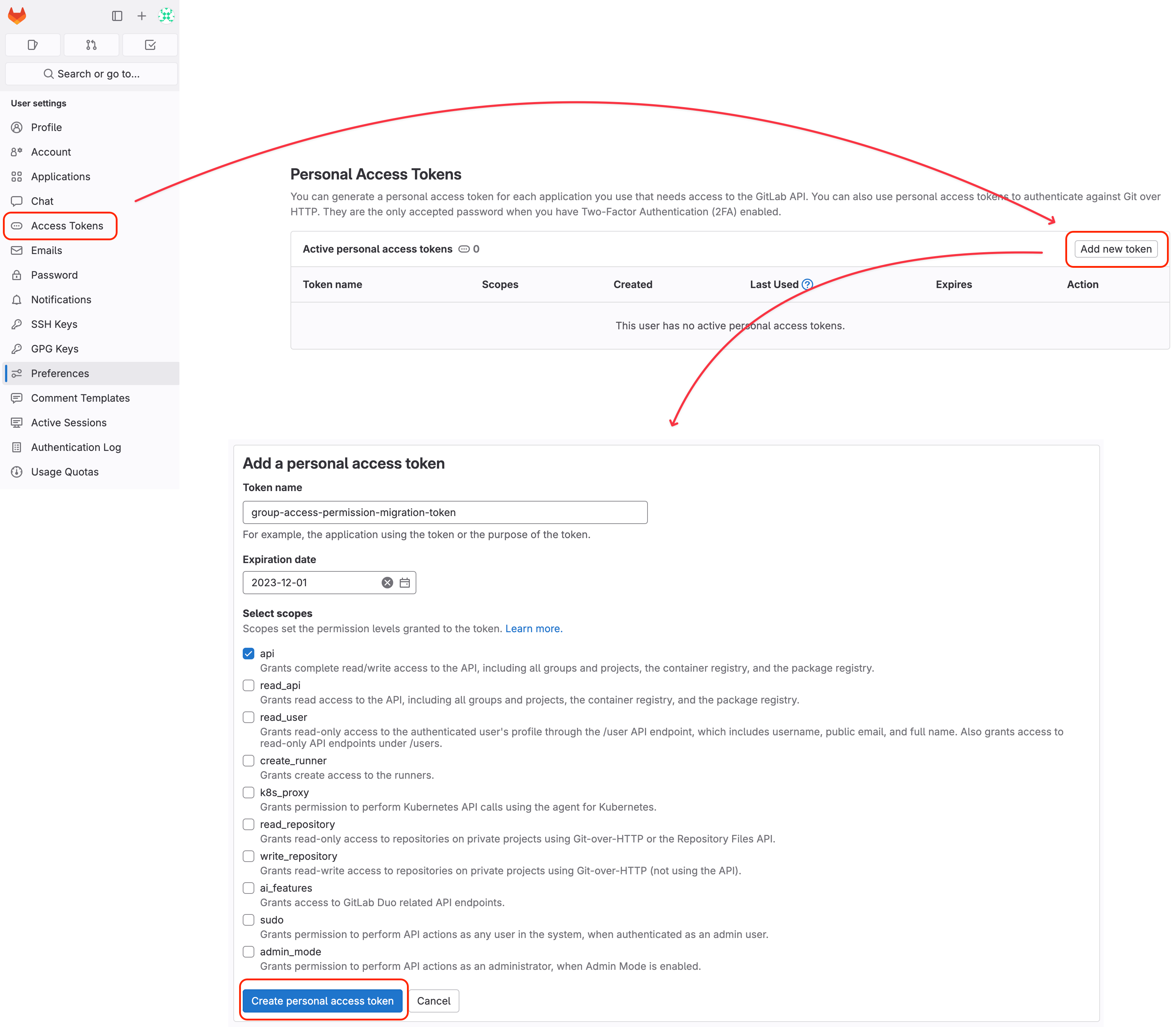
- Securely store the generated token.
3.2 3.2 Preparing and running the script
-
Ensure Python and pip are installed.
-
Install the requests module:
$ pip install requests -
Save the provided script as 'invite_group_to_all_visible_repositories.py'
import sys
import re
import json
from requests import post, get
host = sys.argv[1]
token = sys.argv[2]
group_name = sys.argv[3]
if(host.endswith("/")):
host = host[:-1]
headers = {
"Authorization": f"Bearer {token}"
}
def get_groups():
response = get(f"{host}/api/v4/groups?search={group_name}", headers=headers)
return response.json()
groups = get_groups()
print(json.dumps(groups))
name_matched_groups = [group for group in groups if group["name"] == group_name]
if len(name_matched_groups) == 0:
print(f"couldn't find group that has name {group_name}")
sys.exit(1)
group = name_matched_groups[0]
group_name = group["name"]
payload = {
"group_access": 10,
"group_id": group["id"]
}
NEXT_PAGE_PATTERN = re.compile("<(.+)>; rel=\"next\"")
def get_projects():
projects = []
response = get(f"{host}/api/v4/projects?order_by=id&sort=asc", headers=headers)
projects.extend(response.json())
if "Link" in response.headers:
match_result = NEXT_PAGE_PATTERN.search(response.headers["Link"])
if(match_result):
next_page_url = match_result[1]
else:
next_page_url = None
else:
next_page_url = None
while next_page_url:
response = get(next_page_url, headers=headers)
if "Link" in response.headers:
match_result = NEXT_PAGE_PATTERN.search(response.headers["Link"])
if(match_result):
next_page_url = match_result[1]
else:
next_page_url = None
else:
next_page_url = None
projects.extend(response.json())
return projects
for project in get_projects():
project_id = project["id"]
project_name = project["name"]
share_proejct_endpoint = host + f"/api/v4/projects/{project_id}/share"
response = post(share_proejct_endpoint, json=payload, headers=headers)
if response.status_code == 201:
print(f"proejct {project_name} is shared with group {group_name}")</(.+)> -
Run the script with the following command:
$ python invite_group_to_all_visible_repositories.py {GitLab_host} {user_access_token} {group_name_to_invite}
3.3 Verifying access grant
Check if the group has been successfully invited in each project's 'Manage' → 'Members' → 'Groups' menu.
Important Notes
- All access tokens are confidential information and should be managed securely.
- Tokens should only be used for authorized integration purposes.
- The 'read_api' permission is essential for querying the list of accessible projects.
- When granting multiple project permissions to a group, it only applies to projects accessible by the user.